Functionality and capabilities
Whilst Microsoft Defender’s key functionality is tightly integrated and intertwined between its various capabilities and Microsoft’s other threat protection products, the capabilities of Microsoft Defender ATP can be broadly summarised within the following categories:
Threat & Vulnerability Management
MDATP performs a real-time software inventory on endpoints. It therefore has visibility of all the software on a machine and insights into changes such as patches, installations and uninstallations. Where known security vulnerabilities exist in relation to the applications running on your machines, or where there are missing patches, Microsoft Defender ATP will discover them, prioritise them and allow you to remediate it with security recommendations. Integration between Microsoft Defender ATP with Intune and System Centre Configuration Manager (SCCM) provides a built-in remediation process.
Attack Surface Reduction
By putting certain controls in place with MDATP, you can minimise the areas where cyber threats and attacks could attack your defences. For example, applications must be marked as trusted for them to run, rather than being trusted by default as they might have been in the past. Hardware isolation also reduces the attack surface, isolating untrusted websites and PDFs inside lightweight containers to keep them separate from Windows 10 — protecting the machine and company data from the intruder.
Endpoint Detection and Response (EDR)
The key post-breach functionality of Microsoft Defender ATP is its endpoint detection and response (EDR) capabilities. MDATP detects attacks in almost real-time, providing actionable alerts to IT and security analysts. ‘Alerts’ which share common characteristics (e.g. ‘same file’, ‘same URL’, ‘proximate time’ or ‘file characteristics’ etc.) are automatically grouped together into ‘Incidents’. This aggregation makes it easier for the response team to investigate and respond to threats across the organisation.
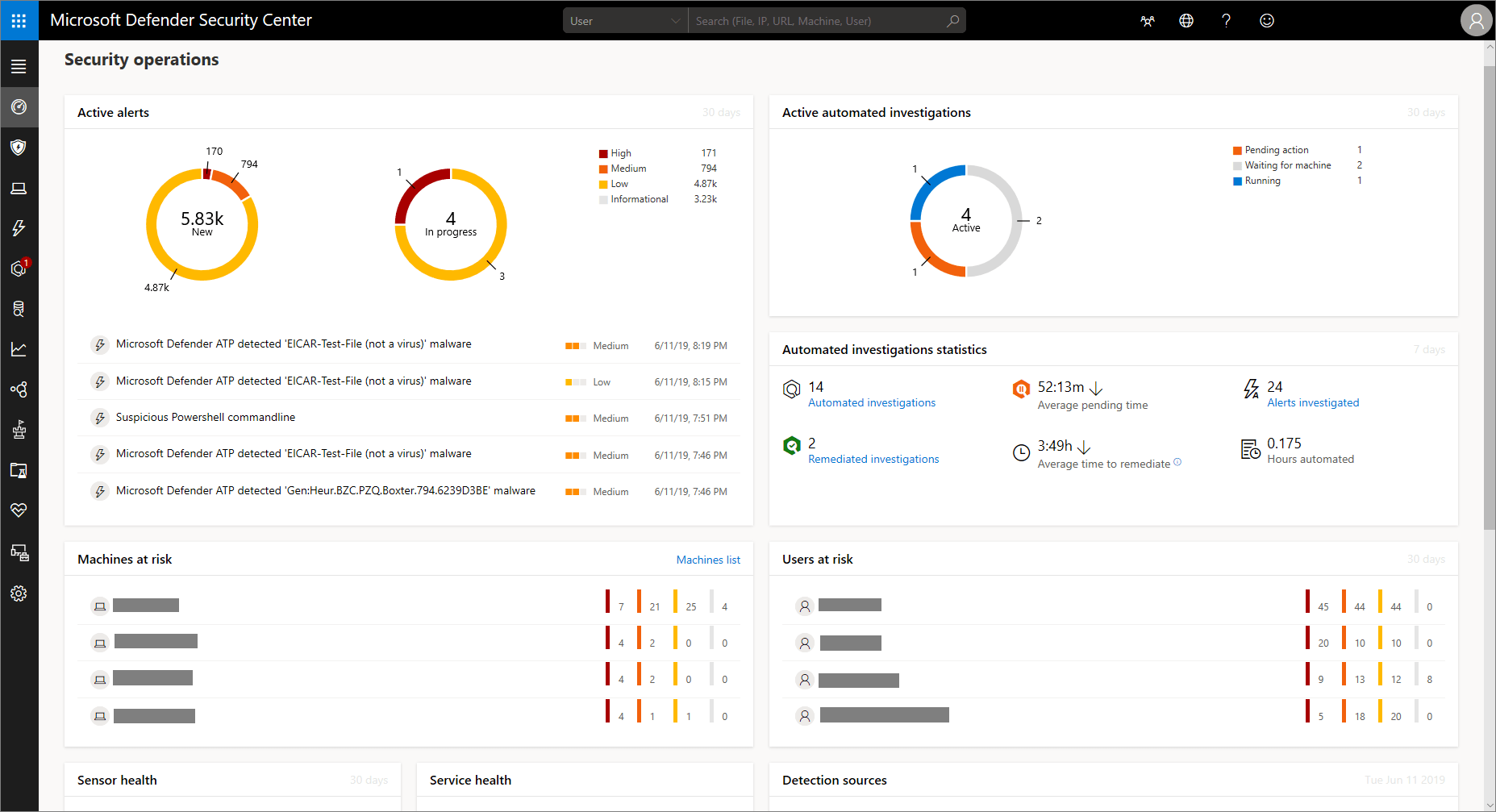
The Microsoft Defender ATP security operations dashboard allows you to explore your organisation’s data in numerous ways from a centralised location. For example, you can view things like machines at risk, users at risk, suspicious activities, active alerts, automated investigations etc all from a high-level dashboard where your company data is surfaced.
Alerts
As threats occur on your endpoints e.g. a malicious executable, you’ll almost instantly receive alerts within the Microsoft Defender ATP dashboard.
The alert will be listed on the dashboard with various metadata attached to it such as: a title, the affected machine name, the user’s name, a severity score and how long it has been in the queue etc.
Investigation
You can then investigate the threat further. Microsoft Defender ATP provides a description of the threat, explaining what has occurred e.g. “A suspicious behavior by Microsoft Word application was observed. The behavior may indicate that a Word document was used to deliver Malware or initiate other malicious activities on the machine”.
You will also see a list of recommended actions on how best to approach the suspicious behavior. Whilst this is useful in order to remove the threat, you will likely also want to know how and why this threat took place.
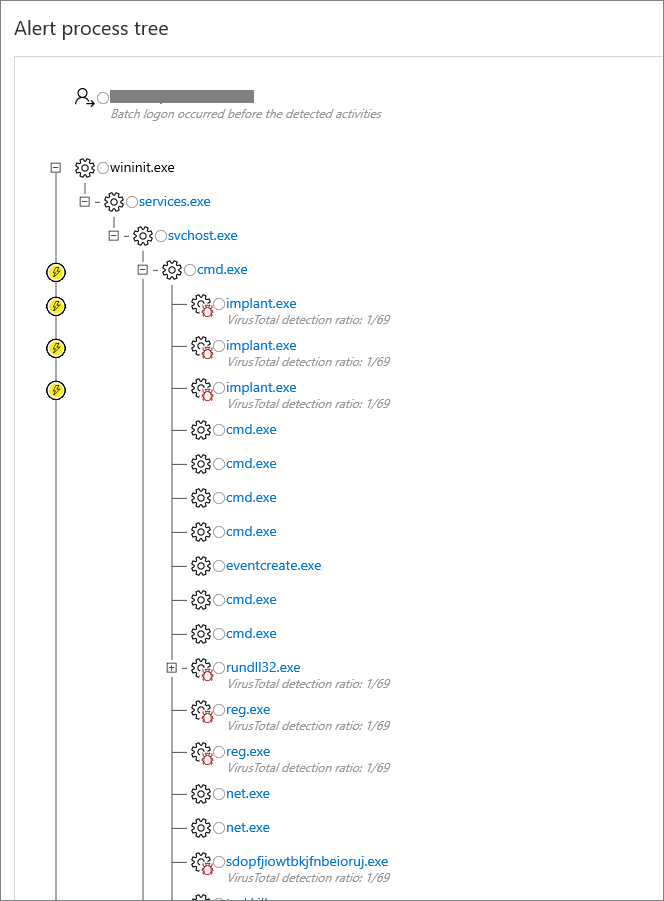
One of Microsoft Defender ATP’s best features is its timeline of events. Within the alert, you can open a timeline which takes the form of a process tree structure, showing you a complete timeline of how the threat arrived on the endpoint and the activities that it has been involved in since appearing on the device.
Remediation
Microsoft Defender ATP allows you to quickly respond to attacks by taking response actions on machines and files. You can then select which actions you want to perform on the alert while you take action to remediate the issue. This can be actions such as running an antivirus scan, restricting app execution or isolating the machine from the network while retaining connection to the Microsoft Defender ATP service.
You also get complete visibility of how the infection spread within your network. Microsoft Defender ATP provides you with a list of all the machines that have been infected since the initial onset of the threat. This allows you to then carry out remediation and investigation on these machines too.
In respect of files. Microsoft Defender ATP allows you to quickly take a file and quarantine it, also providing insights into how many machines the file is on within your organisation, the global prevalence of the file, how many file names there are and the number of instances of the file.
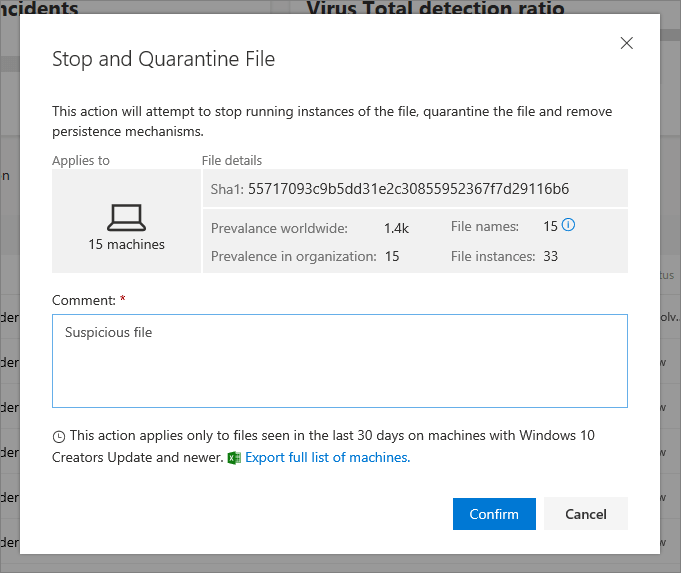
These insights are extremely valuable and enable organisations to successfully remediate threats extremely quickly.
Automated investigation and remediation
Due to the high prevalence of online threats and multiple endpoints across your organisation, the Microsoft Defender ATP service can generate a significant volume of alerts — which can prove challenging for IT teams to keep on top of. Therefore, an automated service is included with Microsoft Defender ATP to examine alerts and resolve security breaches through immediate remediation. This reduces the volume of alerts, allowing security admins to focus on the most pressing issues. Alternatively, you can work with a Security Operations Centre who can triage incoming alerts and highlight high priorities that require immediate action.
Advanced Hunting
With advanced hunting, Microsoft Defender ATP allows you to use powerful search and query capabilities to hunt threats across your organisation. Your custom detection rules are used to generate alerts which appear in your centralised Microsoft Defender Security Centre dashboard.


