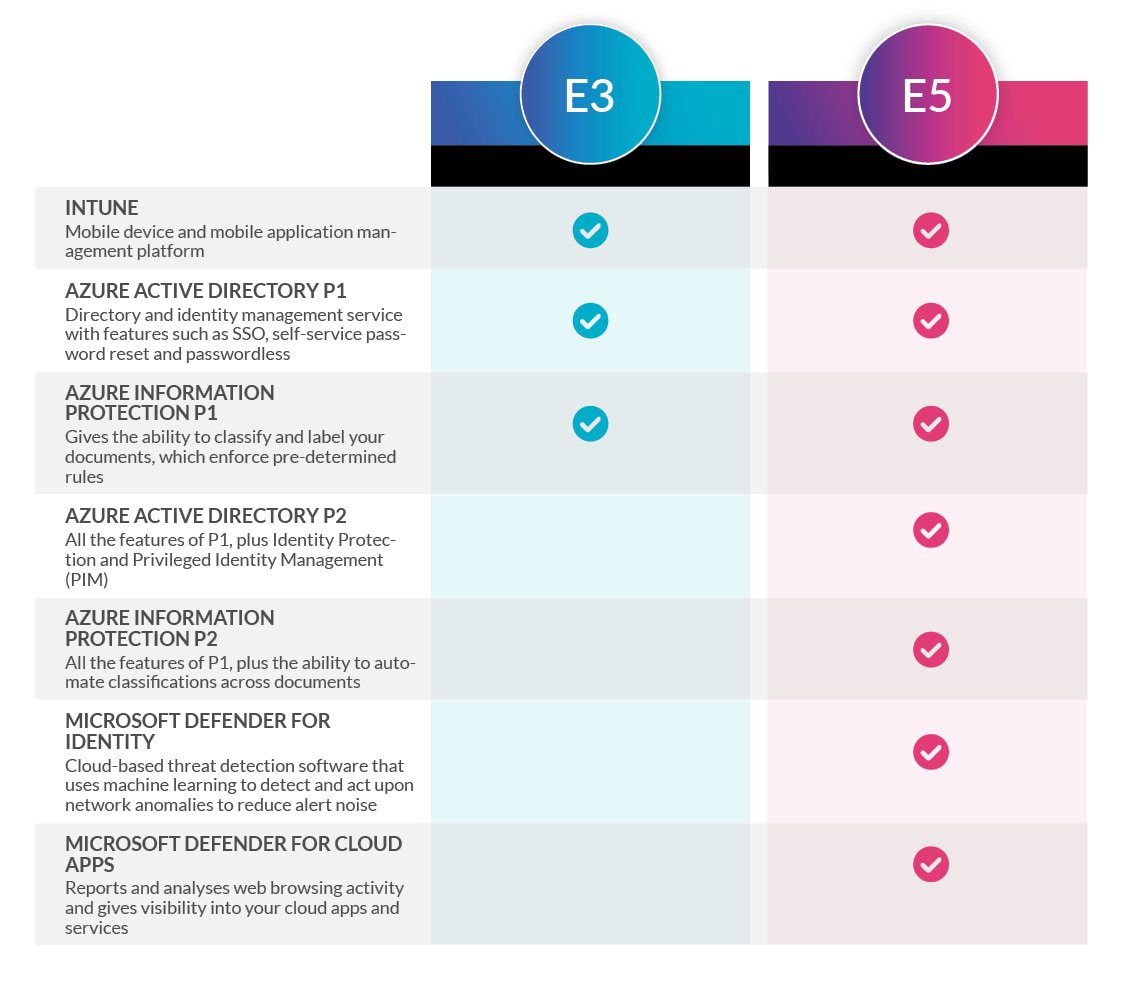
What’s Included?
Azure Active Directory
Azure AD is a cloud-based identity and access management solution from Microsoft. Azure Active Directory comes in four versions: free (included with an Azure subscription) and an Office 365 edition, which provide more basic functionality and then two premium versions: P1 and P2, which are included with EMS (P1 in E3 and P2 in E5) – you can review the complete list of versions and their features here. Key features of Azure AD include:
- Streamlined user experience and logins with single sign-on (SSO) across thousands of SaaS applications
- Elevate security with built-in MFA and apply conditional access policies based on location, device and more to transition to a zero-trust approach (Conditional Access only available for P2 or EMS E5)
- Centralise and simplify identity management with advanced administration capabilities, such as group policies and dynamic groups
- Empower staff and reduce IT overhead with self-service capabilities, such as self-service password reset (SSPR) and application requests
- Integrate Azure AD with other Microsoft services, such as Cloud App Security for holistic security, or allow remote device building with Windows Autopilot and Intune
Intune
Intune is Microsoft’s Unified Endpoint Management (UEM) solution helps to protect and manage your staff devices and data – across mobiles, tablets, laptops and PCs. Key features include:
- Mobile device management across your entire mobile and PC ecosystem (iOS, Android and Windows) as well as all Windows 10 devices – for a complete solution
- Mobile app management to secure business apps and data on personal devices (BYOD) so staff can work securely on whatever device
- Ensure devices and apps are compliant with company security requirements
- Allow ‘zero touch’ IT – so that staff devices can be remotely deployed, reset or wiped to reduce courier costs and speed up efficiency
- Automatically remove threats across all managed endpoint when integrated with Microsoft Defender Advanced Threat Protection
Microsoft Defender for Identities (formerly Azure Advanced Threat Protection)
This is Microsoft’s cloud-based threat detection platform that detects and investigates advanced attacks on your network using machine learning to rapidly alert you of any suspicious activity or anomalies. Key features include:
- Learns typical user behaviour so that only anomalies or important issues are sent; greatly reducing alert noise
- Improves speed of detection and picks up suspicious patterns that would otherwise likely go undetected
- Prioritises risks and displays clear incident information with a simple timeline to make investigation much quicker, easier and more efficient
Microsoft Information Protection
Sometimes referred to as MIP, this solution is for information management and protection and available within EMS as P1 or P2. MIP allows organisations to configure policies and classify their data and then provide persistent protection (using Azure Rights Management) to protect the data wherever it goes – especially important for data governance and compliance. Key features include:
- Ability to apply sensitivity labels and configure policies to tightly control data access and determine what is and isn’t allowed for labels (such as printing, forwarding, etc)
- Automatically search, classify and protect your company documents and files
- Ensure persistent protection so that it doesn’t matter where documents go – they are always protected with your configured rules
- Easily share data with external contacts and have peace of mind that access can be revoked at any point- ideal for sharing data with partners and suppliers
- Gain visibility on all data governance and documentation with powerful reporting and logging
Microsoft Defender for Cloud Apps (formerly Microsoft Cloud App Security)
This is a Cloud App Security Broker (CASB) solution that provides visibility and control over your data across cloud services – Microsoft and third-party services, such as Salesforce, Dropbox etc. With MCAS, you can:
- Discover and control shadow IT – identify third-party apps in usage, review associated risks and compliance, analyse usage and then manage access and controls
- Classify and protect data across your cloud apps – apply policies (or automate labelling) with Azure Information Protection to make data self-protecting wherever it goes
- Detect unusual cloud behaviour to identity and remediate threats (such as compromised users and ransomware) with alert scoring and remediation actions
- Review your cloud app compliance – check the compliance risk of various cloud apps and drill into app usage to assess risk